
Here's how to protect your account and identity.
Secure your BancFirst account
Take precautions online
Financial education resources
Let's work together to secure your BancFirst accounts.
We go online for everything from shopping and communicating to banking and bill paying. While the benefits of more convenient services are clear, the strategies for preventing online fraud and theft may not be as well-known. We want you to be aware of fraudulent situations so you can make informed online decisions. Before we get into the various types of scams, here are 2 quick tips to protect and monitor your bank account:
- BancFirst's Debit Card Controls allow you to help safeguard your debit card from fraud by blocking authorizations, setting alerts, establishing spending limits, and controlling transaction types.
- Set up mobile banking alerts and notifications on our online banking page. Alerts can notify you on low balance, large withdrawal, loan payment date, and more.
For a broader understanding of CyberSecurity, please view the FDIC's Consumer Assistance Topics page: https://www.fdic.gov/resources/consumers/consumer-assistance-topics/cybersecurity.html
Tips for avoiding a scam:
- Block unwanted calls and text messages.
- Don't give your personal or financial information in response to a request that you didn't expect.
- Resist the pressure to act immediately.
- Be alert if someone asks you to pay them via cryptocurrency, Western Union, wire transfer, or gift cards.
- Stop and talk to someone you trust.
Signs they're a Scammer:
- Pretend to be from an organization you know
- Say there's a problem or a prize
- Pressure you to act immediately
- Tell you to pay in a specific way
Resources on how to identify and avoid scams:
- How To Avoid a Scam | Consumer Advice (ftc.gov)
- Mobile-friendly PDF: FTC-How-to-Avoid-a-Scam.pdf
Stop cryptocurrency scams before they start.
Do any of the following scenarios sound familiar?
- Were you encouraged to send cryptocurrency to repair a virus on your computer?
- Were you told the only way to protect your money was by making deposits to cryptocurrency ATMs?
- Did someone ask you to lie to the bank or keep the reason for your cryptocurrency purchase a secret?
- Are you in a relationship with someone online who is asking you to send them cryptocurrency purchased at an ATM?
- Has anyone promised high returns on a cryptocurrency investment?
- Did someone representing a government agency or law enforcement organization call and request you provide cryptocurrency to satisfy a warrant, fine, or to post a bond for a relative in jail or prison?
If you have been targeted or sustained a loss due to a cryptocurrency scam you should immediately report it to Internet Crime Complaint Center, and then call our Customer Support to discuss further.
Fraudsters use multiple techniques to manipulate a victim into disclosing information or taking a specific action. Or, as the FBI has stated, “… social engineering—or, more bluntly, targeted lies designed to get you to let your guard down.”
Social engineering is the use of deception, through manipulation of human behavior, to target and manipulate you into divulging confidential or personal information and using it for fraudulent purposes. In the context of information security, social engineering might also mean psychologically manipulating people to take action to inadvertently give adversaries access to protected information or assets.
Common social engineering attacks:
- Phishing – Emails claim they are from a trusted source
- Technical Support Phone Calls – Phone calls trying to obtain passwords or install software
- Business Email Compromise – Fraudsters using your email to attempt fraud
- Social Media Fake Users – Using social media to gain trust with you or customers
Fraudsters are attempting to:
- Gain access to your computer to introduce malware, such as ransomware
- Attempt ACH or wire fraud
- Obtain sensitive information
- Persuade you to send them money through gift card
How to not fall victim to social engineering:
- Do not give out personal information, such as account numbers or credit card information, unless you have initiated the conversation or activity (i.e. visited a specific website).
- Do not give your username or password to anyone.
- Do not install software on your device as a result of (or at the request of) an unsolicited call from a technician.
There are an estimated 294 million smartphone users in the US, making these devices an attractive target for cybercriminals. The threats are basically the same as on your desktop PC or laptop, but mobile devices are usually turned on all the time, you carry them with you, and the text feature creates an added layer of vulnerability.
What are examples of mobile threats?
Mobile Spyware
Spyware is a type of malicious software that monitors and records information about a user's actions without the user's knowledge or permission. Once the victim of the malware attack has been affected by mobile spyware, the intruder is able to listen in on conversations, access data stored on the mobile device, and can even tap into the device’s camera and microphone.
Mobile Banking Trojans
This invasive malware hacks into your mobile banking app in an attempt to steal information and money from your bank account. Anyone who has a mobile banking application installed on their mobile device is at risk of falling victim to these trojans, however Android users are at a higher risk of being attacked. Mobile trojans are hard to detect because they are disguised as legitimate applications.
SMS Malware
SMS malware can affect any device that is able to receive calls and/or text messages and is installed by sending unauthorized calls or texts without the victim’s knowledge. This malware may also intercept text messages or calls without the user’s consent.
How to protect your Mobile Device:
- Keep your phone operating system up to date; install the latest version when prompted.
- Keep all of your apps up to date.
- Use strong device authentication. Additionally, enable two-factor authentication on apps and websites when available.
- Use secure networks. Avoid public or unknown Wi-Fi systems.
- Install security software often offered by your cellular carrier.
These are other resources to consider:
1. CISA-Capacity-Enhancement-Guide-Mobile-Device-Cybersecurity-Checklist-for-Consumers
When bank employees are working with a customer over the phone, several steps must be taken to validate or authenticate the identity of the customer. To expedite the process, ask your local bank representative to set up an authentication code and register your cell phone number.
Hackers have published over 555 million stolen passwords on the dark web. And 80% of hacking incidents are caused by stolen or reused login information. Authentication to online applications is a serious concern to anyone who uses the Internet.
Multi-factor Authentication (MFA) – a safer way to sign in to your online accounts. Authentication is the mechanism that a website or application uses to verify who you are and what access you have. Simple authentication is in the form of a username and password – the same information that is stolen on the dark web. Multi-factor Authentication (MFA) provides an added layer of security to your accounts by requiring a second method of verification after you enter your password. The second level verification often comes via text providing a one-time passcode to further validate your credentials. How to protect your online access:
-
Do not share your username and password with anyone. Many scams include a “technician” who calls and asks for your username and password to help you with a site. Do not share information giving anyone access to your personal information.
-
Use a password phrase for extra security. For example, use a long title of a movie replacing and capitalizing different letters: CatchM3ifyouc@n.
-
Use a password manager app to store and manage your passwords. These applications can maintain your list of usernames and passwords with different websites.
-
Do not use the same password on multiple sites. A common username is an email address. If you use the same email address and password, this will give a hacker access to all those websites or applications.
-
If given the option, use multi-factor authentication.
Resources:
- This site can tell you which accounts associated with your email address have been hacked: https://haveibeenpwned.com
Business Email Compromise (BEC) is a sophisticated scam commonly targeting businesses through spoofed email accounts in order to modify or generate fund transfers, such as wires or ACH, so that the funds arrive at the scammer’s bank account or money mule account!
In a BEC scam, criminals send an email message that appears to come from a known source making a legitimate request, like in these examples:
- A vendor your company regularly deals with sends an invoice with an updated mailing address.
- A company CEO asks her assistant to purchase dozens of gift cards to send out as employee rewards. She asks for the serial numbers so she can email them out right away.
- A homebuyer receives a message from his title company with instructions on how to wire his down payment.
Versions of these scenarios happened to real victims. All the messages were fake. And in each case, thousands—or even hundreds of thousands—of dollars were sent to criminals instead.
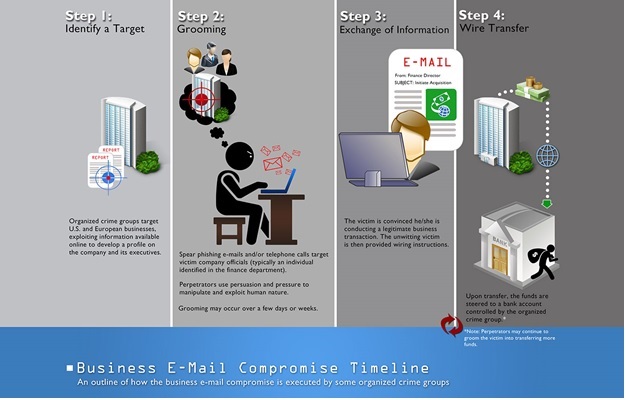
Scammers might:
Spoof an email account or website. Slight variations on legitimate addresses (john.kelly@examplecompany.com vs. john.kelley@examplecompany.com) fool victims into thinking fake accounts are authentic.
Send spearphishing emails. These messages look like they’re from a trusted sender to trick victims into revealing confidential information. That information lets criminals access company accounts, calendars, and data that gives them the details they need to carry out the BEC schemes.
Use malware. Malicious software can infiltrate company networks and gain access to legitimate email threads about billing and invoices. That information is used to time requests or send messages so accountants or financial officers don’t question payment requests. Malware also lets criminals gain undetected access to a victim’s data, including passwords and financial account information.
Tips for Preventing BEC:
- Be wary of email-only wire transfer requests and requests involving urgency.
- Establish a reliable phone number of the entity you are doing business with and call them confirming your wiring or transaction information.
- Don’t click on anything in an unsolicited email or text asking you to update or verify account information. Use a known good phone number to verify with the company if the request is legitimate.
- Inspect the email for a mimicked email addresses.
- Use multi-level authentication.
Resources:
Mastercard's ID Theft protection provides a preventative service to its debit card holders. The service alerts when personal information, such as your Social Security number, debit card number or and email address, is known to be compromised. Click here to learn more about Mastercard's ID Theft protection service.
Click the link below to read BancFirst's tips on mitigating common Consumer Scams:
Consumer Scams HandoutBancFirst prioritizes the security of the people we care about: our family, customers, and communities.
We want to bring to your attention a recent scam targeting our customers. Fraudulent text messages claiming to be from BancFirst are being sent out and followed by phone calls impersonating BancFirst.
What you need to know:
- Customers receive a text message that appears to be from BancFirst (see example below).
- Fraudsters follow up with a phone call that appears to come from our number.
- During the call, fraudsters attempt to collect sensitive information, such as:
- Debit or credit card numbers
- Social Security numbers
- Dates of birth
- Other personal or financial details
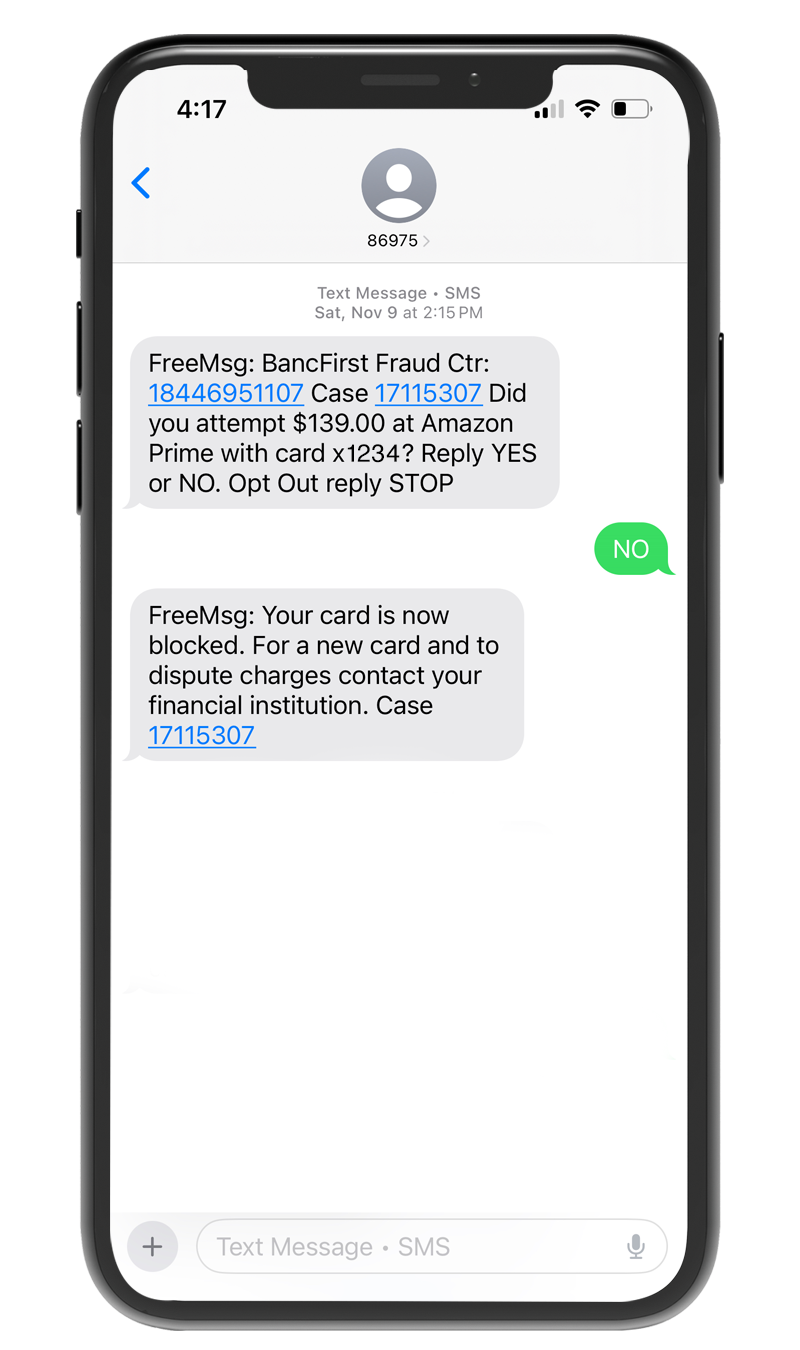
We will never ask for your sensitive information (e.g. card numbers, SSN, or passwords) via text or over the phone. Any requests of this nature are fraudulent.
Tips to Protect Yourself:
- Do not respond to suspicious texts.
- Do not share personal or financial information over the phone.
- Verify the source of any communication. If you have any doubts, please contact our Customer Support:
- Contact your financial institution immediately. If you've shared personal information and later realized it could have been fraudulent, contact us immediately so we can assist you.
